Ask any veteran PI and they’ll tell you the last five years delivered more change than the prior twenty. Now the pace is accelerating. From quantum-resistant encryption to hyper-realistic synthetic media, tomorrow’s threats require a radical rethink of tools, skills, and even ethics. At F3 Investigations, we’re not just watching trends—we’re engineering for them. Below is our forecast of what’s coming and how we’re preparing to keep you ahead of the curve.
1. Quantum-Ready Cryptography
Commercial quantum computers inch closer to cracking today’s public-key encryption, potentially exposing decades of stored communications [1]. We’re migrating evidence archives to NIST-recommended post-quantum algorithms and deploying hybrid VPN tunnels that can be upgraded mid-session without packet loss.
2. AI-Generated Deception at Scale
Generative models already craft voice-cloned phone calls and “photographs” of events that never happened [2]. Courts face an authenticity crisis. We’ve added GAN-detection suites and provenance-tracking watermarks to our lab and train examiners in C2PA media-forensics protocols [3].
3. Privacy-First OS Ecosystems
Apple Lockdown Mode and Android Private Space signal a future where mainstream devices reveal far less telemetry [4]. Our endpoint analytics infer activity patterns without over-collecting personal data, keeping us compliant with evolving privacy laws.
4. Drone & IoT Expansion
By 2026, 7 billion connected “things” will capture continuous video, audio, and sensor data [5]. We’re building sensor-fusion platforms that merge drone footage, smart-camera metadata, and location pings into unified timelines—while preserving chain of custody.
5. Global Data Localization
Forty-eight countries now require certain evidence to stay within their borders [6]. We maintain regional data lakes in compliant cloud zones and partner with licensed in-country investigators for on-site collections, protecting admissibility from Seoul to São Paulo.
6. Insider Threat 2.0
Remote work and AI copilots make it easier for disgruntled employees to siphon data and mask tracks with auto-generated logs [7]. We embed invisible canary tokens in sensitive files; if those tripwires phone home, attribution is instant and immutable.
The Evolving Nature of Evidence
 Evidence is no longer purely binary—fingerprint present or not, signature real or forged. We’re entering a world of probabilistic proof: a report might state that a video is “94.7 % likely to be synthetic” based on GAN-artifact analysis [8]. Our job expands from finding data to translating statistical authenticity into courtroom-ready testimony that judges and juries can trust.
Evidence is no longer purely binary—fingerprint present or not, signature real or forged. We’re entering a world of probabilistic proof: a report might state that a video is “94.7 % likely to be synthetic” based on GAN-artifact analysis [8]. Our job expands from finding data to translating statistical authenticity into courtroom-ready testimony that judges and juries can trust.
Profile of a Next-Generation Investigator (2030)
Hybrid by Design. Our 2030 operative is equal parts digital-forensics examiner and field investigator. They understand post-quantum algorithms, hold a commercial drone license, can testify on sensor-data chain of custody, and wield computational-linguistics models that flag AI-generated text. Yet they’re also classic rapport-builders—able to read body language in a world wary of deep-fakes. Tech augments them; human acuity still closes the case.
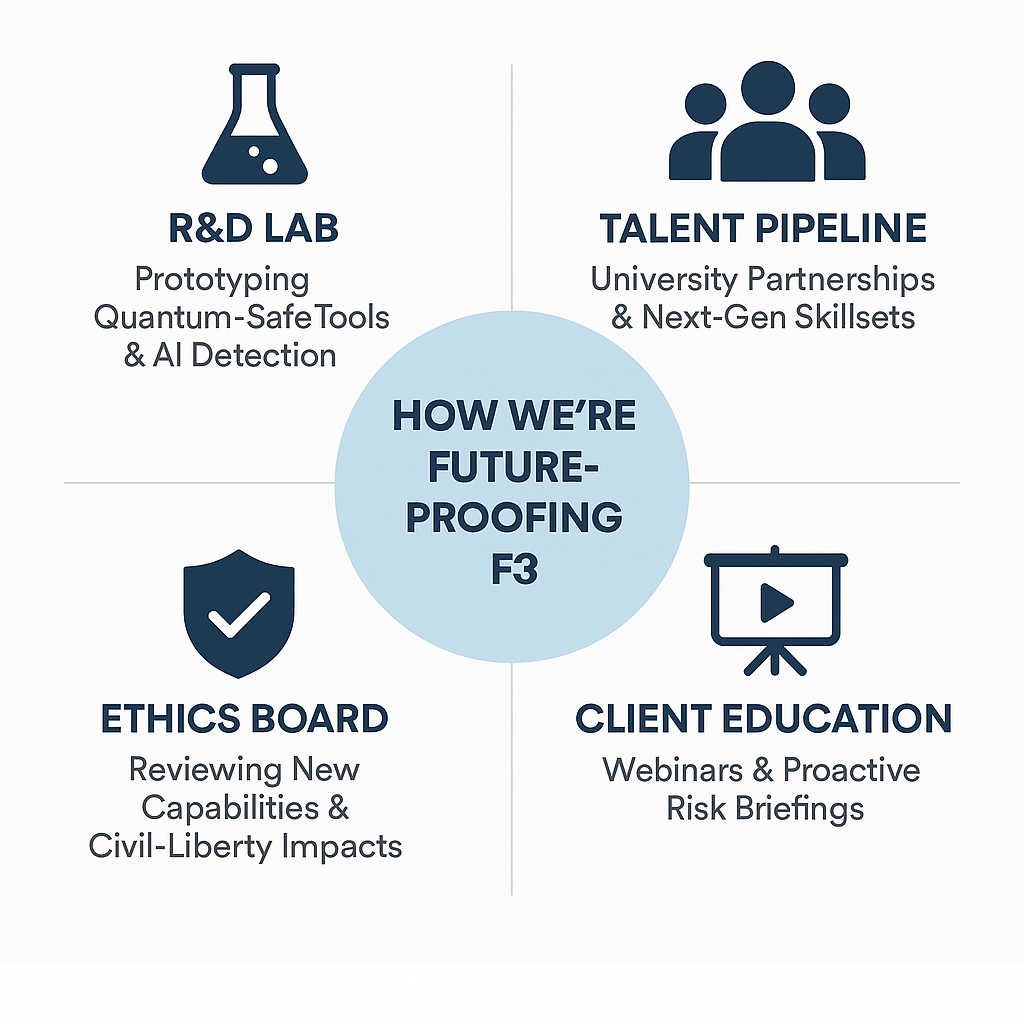
How We’re Future-Proofing F3 Today
- R&D Lab Upgrades: 25 % of our annual budget funds tool prototyping—quantum-safe storage, multimodal AI detection, and drone-evidence workflows.
- Talent Pipeline: University co-op rotations in threat intel and linguistics keep skills fresh.
- Ethics Board: A five-member panel (legal, tech, investigative, privacy, bioethics) reviews each new capability for civil-liberty impact.
- Client Education: Quarterly webinars demystify emerging risks so legal teams and insurers can adapt policies before crises hit.
Tomorrow’s adversaries won’t wait for us to catch up—and neither should you. Whether you’re preparing for complex litigation, safeguarding IP, or future-proofing corporate security, we’re already testing the gear, writing the SOPs, and hiring the specialists to keep your case on the cutting edge—legally and ethically.
Reference List
- National Institute of Standards and Technology. “Post-Quantum Cryptography Standardization Project: Status Update 2025.” https://csrc.nist.gov/projects/post-quantum-cryptography
- Europol. “Facing Reality? Law-Enforcement Challenges of Synthetic Media” (2024). https://www.europol.europa.eu
- Coalition for Content Provenance and Authenticity (C2PA). Technical Specification v1.3 (2025). https://c2pa.org
- Gartner. “Top Mobile Security Trends for 2025.” https://www.gartner.com
- International Data Corporation. “Worldwide IoT and Drone Camera Forecast, 2024–2028.” https://www.idc.com
- Deloitte. “Data Localization Laws 2025: Navigating the Patchwork.” https://www2.deloitte.com
- Verizon. “2025 Data Breach Investigations Report: Insider Threat Edition.” https://www.verizon.com/business/resources/reports/dbir-insider-threat-2025
- Harvard Journal of Law & Technology. “Probabilistic Evidence and Admissibility in the Age of Deep Fakes” (2024). https://jolt.law.harvard.edu