Digital evidence is everywhere yet often nowhere in plain sight. A wiped phone, a reformatted laptop, or a self-destructing chat app might look empty to the casual observer, but to trained examiners with the right toolkit, those “blank” devices are treasure troves. At F3 Investigations, we pair cutting-edge lab gear with courtroom-tested methodology to reveal what wrong-doers assume is gone forever. Below is a tour of the techniques we rely on most.
1. Volatile-Memory Forensics – The Whiteboard Analogy
Live RAM is the crime scene that disappears when you power down. Picture a busy meeting room where ideas are scribbled on a whiteboard; when the meeting ends, the board is wiped clean. Our cold-boot kits and memory-dump agents act like an instant camera, photographing that whiteboard before it’s erased—capturing passwords, encryption keys, and live network sessions the moment before they vanish. Modern frameworks like Volatility 3 let us map those snapshots to MITRE ATT&CK tactics for rapid attribution [1].
2. Timeline Reconstruction & Artifact Fusion
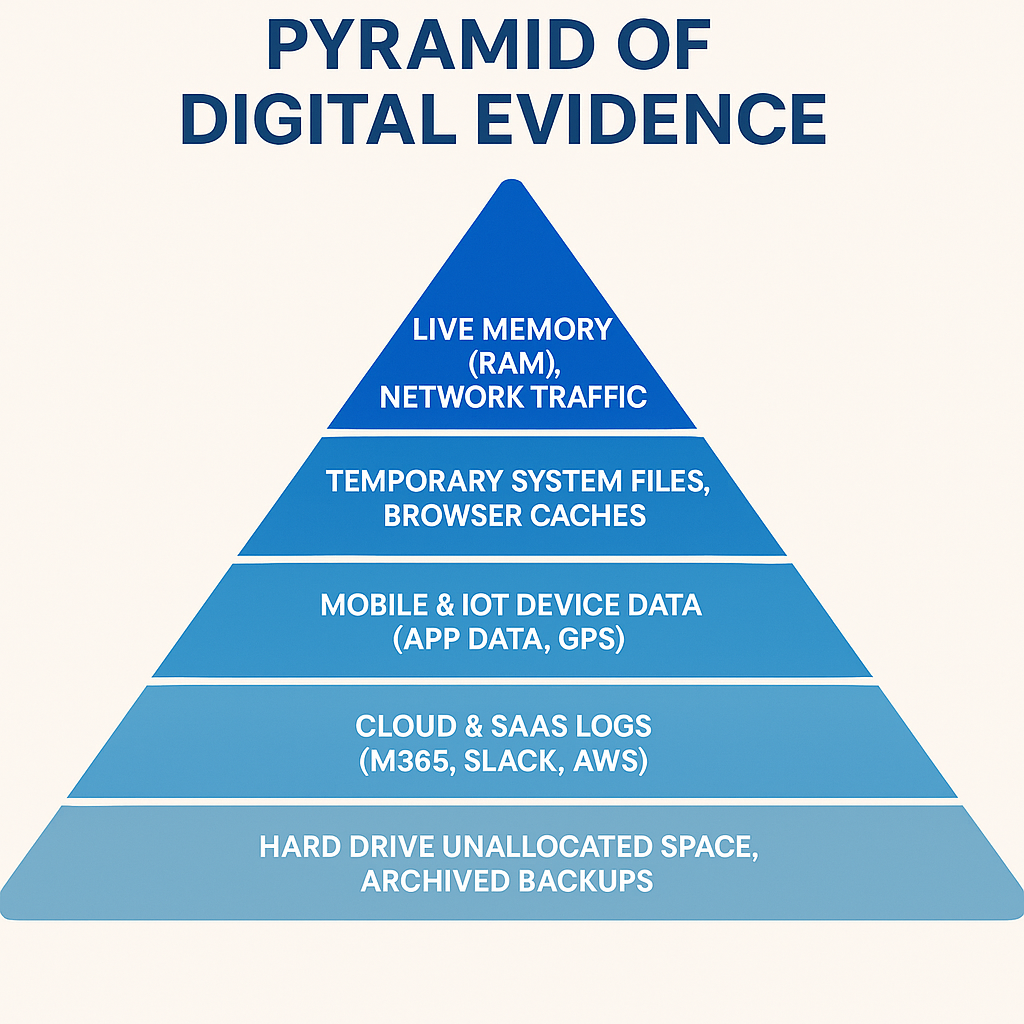 Windows Prefetch, macOS Unified Logs, browser caches—each tells only part of the story. Our timeline engines ingest thousands of artifacts and fuse them into minute-by-minute narratives. One SANS case study found multi-source timelines cut incident-response time by 38 percent [2].
Windows Prefetch, macOS Unified Logs, browser caches—each tells only part of the story. Our timeline engines ingest thousands of artifacts and fuse them into minute-by-minute narratives. One SANS case study found multi-source timelines cut incident-response time by 38 percent [2].
3. Cloud & SaaS Forensics
Data rarely sits on a single hard drive anymore; it lives in Microsoft 365, Slack, or AWS S3. We pull audit logs, file-version histories, and geo-location metadata—even after users try to purge them. NIST now classifies these “off-prem” logs as primary evidence sources [3].
4. Mobile & IoT Extractions
Smartphones, wearables—even smart thermostats—multiply evidence vectors. Chip-off and JTAG techniques bypass damaged or locked devices, while specialised parsers decode encrypted messaging data. Europol reports a 57 percent jump in criminal cases hinging on IoT data between 2022 and 2024 [4].
5. File-Carving & Deep-Carve Analytics – The Librarian Analogy
When a file is “deleted,” the system merely tears out the table-of-contents page that points to it. The pages themselves linger in the recycle bin of unallocated space. Our deep-carve tools are like meticulous librarians: they recognise the font, paper stock, and sentence structure of every loose page, then painstakingly re-assemble the original book—JPEGs, PDFs, even fragmented video.
6. Malware Reverse Engineering
Sometimes the smoking gun is malicious code itself. Sandbox detonation and static disassembly reveal command-and-control endpoints and embedded credentials, feeding indicators back into our threat-intel pipeline [5].
7. Blockchain & Crypto Tracing
Criminals love crypto’s perceived anonymity. We trace coin flows across Bitcoin, Ethereum, and privacy chains using address-clustering heuristics and multi-hop graph analytics. In 2024, the IRS credited blockchain forensics with recovering $10 billion in undeclared gains [6].
Beyond the Tools: The Forensic Analyst’s Mindset
Technology alone doesn’t solve a case—people do. Our examiners marry relentless curiosity with disciplined methodology. They don’t just collect data; they interrogate it: Why did this user access a client file at 3 a.m.? What does a burst of deleted logs right after a VPN connection tell us? It’s this fusion of human pattern-recognition and technical precision that turns raw bytes into a coherent, defensible narrative.
Why Chain-of-Custody Is Our North Star
Every image we capture is hashed (SHA-256), logged, and sealed. Our workflows align with NIST SP 800-86 and DOJ best practices, ensuring evidence holds up under the harshest cross-examination [7].
When to Call Us
Insider-threat probes, IP theft, crypto fraud, civil e-discovery—any scenario where “there’s nothing left” feels suspicious. Digital traces never truly vanish; they simply require the right light (and librarian-level patience) to reveal them. If you’re staring at blank screens and big questions, let’s talk.
Reference List
- Volatility Foundation. Volatility 3 Framework Documentation (2024). https://www.volatilityfoundation.org
- SANS Institute. CASE Study: Multi-Source Timelines in Incident Response (2023). https://www.sans.org
- National Institute of Standards and Technology. NIST SP 800-220: Guide to Cloud Forensics (2024). https://www.nist.gov
- Europol. Internet Organised Crime Threat Assessment (IOCTA) 2024 (2024). https://www.europol.europa.eu
- MITRE Engenuity. Reverse Engineering Malware for Incident Response (2023). https://www.mitre-engenuity.org
- Internal Revenue Service Criminal Investigation. Annual Report 2024 (2024). https://www.irs.gov
- U.S. Department of Justice. Digital Evidence in the Courtroom: A Guide for Law Enforcement and Prosecutors (2023). https://www.justice.gov