For many investigators, October’s Cybersecurity Awareness Month is about patching servers and avoiding phishing links. For us, it’s also about a quieter threat: cyberstalking—persistent, unwanted digital surveillance or harassment that can jump offline without warning. Nearly 40 percent of U.S. adults have endured severe online harassment, and women are twice as likely to face sustained stalking behaviors [1]. We blend digital forensics, threat-intelligence platforms, and old-school gumshoe work to shut these predators down—legally and decisively.
Understanding the Adversary’s Motivation
To counter a cyberstalker, we first profile why they stalk:
- The Obsessed Ex-Partner – Driven by control issues or an inability to accept a breakup.
- The Disgruntled Colleague – Fueled by workplace grievances or professional jealousy.
- The Ideological Agitator – Targets victims for their public views or affiliations.
- The Thrill-Seeker – Harasses at random for power, entertainment, or escalation [7].
Pinpointing motive helps us predict next moves and tailor counter-measures accordingly.
Our Advanced Counter-Stalking Playbook
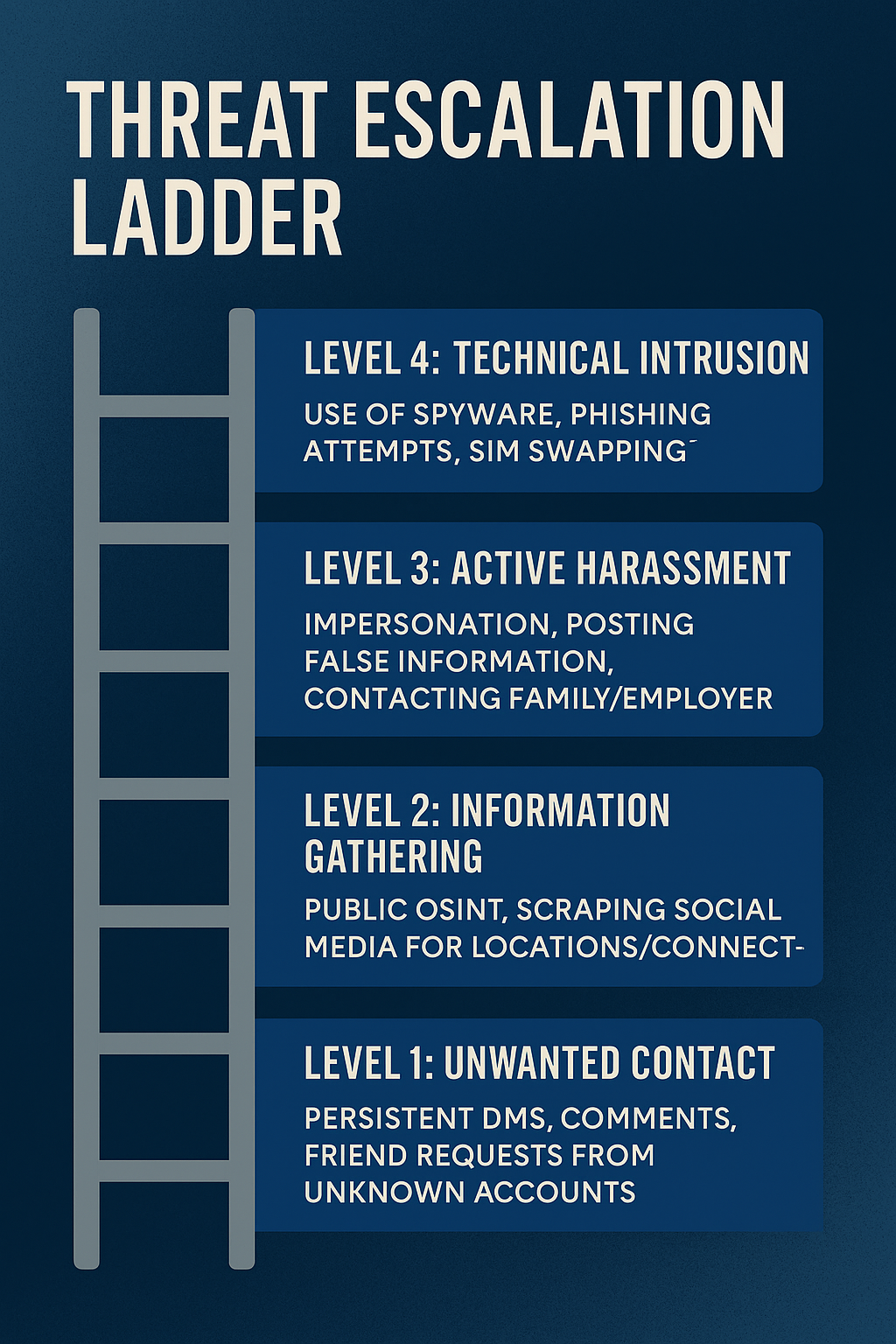
Threat-Surface Audit – A deep OSINT sweep reveals where a stalker gathers intel and where we must cut the feed.
Device & Network Hardening – We scan for stalkerware, lock SIM changes at carriers, and deploy hardware MFA [3].
Honeytokens & Canaries – Decoy data lets us trace leaks back to the stalker in real time [4].
Behavioral Fingerprinting – Stylometry and posting cadence link “new” burner accounts to the same perpetrator [5].
Legal Coordination – We package screenshots, hashed logs, and expert affidavits for subpoenas and restraining orders [6].
Common Roadblocks & Our Solutions
| Challenge | Our Response |
|---|---|
| Spoofed VPN/IP masks identity | Correlate log-in timestamps with honeytoken pings; subpoena exit-node providers |
| Burner social accounts appear daily | Stylometric AI clusters language quirks to one author, proving continuity |
| Victim’s data plastered on breach sites | Rapid takedown requests + automated data-broker removals every quarter |
A Quick Vignette
 An anonymous harasser created fresh Instagram handles every night to threaten our client. Using stylometric fingerprints, we linked the language patterns to a single local individual—despite 40 different account names. The evidence secured an emergency protective order within 48 hours.
An anonymous harasser created fresh Instagram handles every night to threaten our client. Using stylometric fingerprints, we linked the language patterns to a single local individual—despite 40 different account names. The evidence secured an emergency protective order within 48 hours.
Proactive Steps You Can Take Today
- Scrub data-broker sites quarterly.
- Replace SMS 2FA with a physical security key.
- Use segmented email/phone aliases for high-risk accounts.
- Strip location EXIF from photos before posting.
- Freeze credit and lock SIM changes if harassment escalates.
Navigating the Ethical & Legal Maze
Public genealogy, AI analytics, and deep-packet inspections raise privacy stakes. We follow ISOGG and DOJ best-practice guidelines, keep transparent audit trails, and partner with counsel to ensure every byte of evidence is court-defensible [2][6].
Please Note: If you believe you’re in immediate physical danger, contact local law enforcement or a national domestic-violence hotline first. Our services complement—not replace—emergency protection.
How We Help—Beyond DIY
Cyberstalkers pivot fast. We stay faster, monitoring dark-web chatter, updating threat intel, and adapting counter-measures as tools evolve. When someone weaponizes tech to invade your life, we unmask them and restore control.
Reference List
- Pew Research Center. The State of Online Harassment 2024. https://www.pewresearch.org/internet/2024/05/07/the-state-of-online-harassment
- Electronic Frontier Foundation. Commercial Spyware and Stalkerware Explained (2023). https://www.eff.org/pages/spyware-stalkerware
- Cybersecurity & Infrastructure Security Agency. Mobile Device Security Best Practices (2024). https://www.cisa.gov/mobilesecurity
- Krebs on Security. “Using Canary Tokens to Catch Snoops” (2023). https://krebsonsecurity.com/2023/11/using-canary-tokens-to-catch-snoops
- MIT Media Lab. Stylometry and Online Identity Attribution (2024). https://www.media.mit.edu/projects/stylometry/overview/
- U.S. Department of Justice. Cyberstalking and the Law: A Prosecutor’s Guide (2023). https://www.justice.gov/criminal-ccips/cyberstalking-guide
- Journal of Threat Assessment & Management. Motivational Typologies in Cyberstalking Offenders (2023). https://doi.org/10.1037/tam0000157